Note
The Funtoo Linux project has transitioned to "Hobby Mode" and this wiki is now read-only.
Difference between revisions of "Encrypted funtoo on linode"
Jump to navigation
Jump to search
Knightgats (talk | contribs) |
Knightgats (talk | contribs) |
||
| (17 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
This howto describes how to setup a complete Funtoo Encrypted Install ( Root File System and SWAP ) using LUKS and LVM on '''LINODE VPS''' | This howto describes how to setup a complete Funtoo Encrypted Install ( Root File System and SWAP ) using LUKS and LVM on '''LINODE VPS''' | ||
<br /> | <br /> | ||
<big>'''Setting Linode'''</big> | |||
<big>Setting Linode</big> | |||
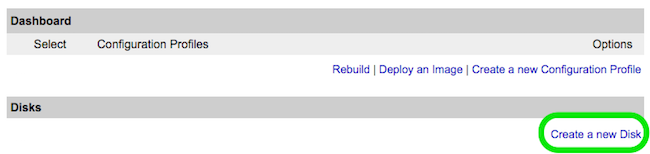
* ''From [https://manager.linode.com/ Linode Manager] create a new Linode. Under the '''Disks''' section of the Linode Dashboard, click on '''"Create a new Disk:"''''' | * ''From [https://manager.linode.com/ Linode Manager] create a new Linode. Under the '''Disks''' section of the Linode Dashboard, click on '''"Create a new Disk:"''''' | ||
[[File:Custom-distro-new-disk small.png|New_Disk]] | [[File:Custom-distro-new-disk small.png|New_Disk]] | ||
<br /> | <br /> | ||
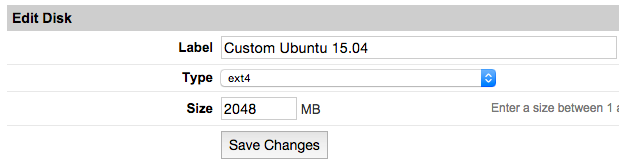
* ''Label your new disk image and choose an appropriate size. Here we will create "two disks" the first for root partition and another for swap. Set appropriate size for each one.'' | * ''Label your new disk image and choose an appropriate size. Here we will create "two disks" the first for root partition and another for swap. Set appropriate size for each one.'' | ||
[[File:Custom-distro-disk-image.png|Edit_Disk]] | [[File:Custom-distro-disk-image.png|Edit_Disk]] | ||
<br /> | <br /> | ||
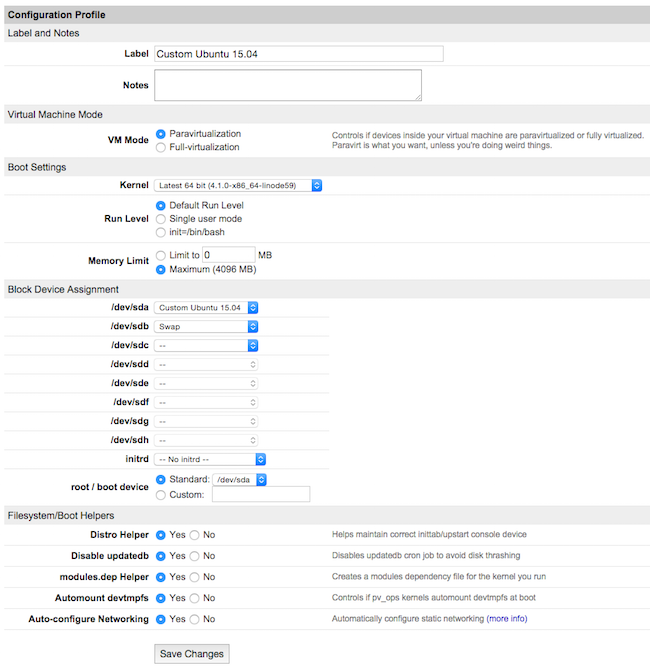
* ''Select the '''Create a New Configuration Profile''' option. Assign a label, and select your disk images under '''Block Device Assignment'''.'' | * ''Select the '''Create a New Configuration Profile''' option. Assign a label, and select your disk images under '''Block Device Assignment'''.'' | ||
[[File:Custom-distro-config-profile small.png|Config_Profile]] | [[File:Custom-distro-config-profile small.png|Config_Profile]] | ||
<br /> | <br /> | ||
Click on '''Save Changes''' once your profile is complete. | Click on '''Save Changes''' once your profile is complete. | ||
| Line 36: | Line 32: | ||
<br /> | <br /> | ||
< | {{Note| Use [[Install|Funtoo Install Guide]] for Reference.}} | ||
* '''MBR Partition layout''' | |||
<pre> | |||
Device Boot Start End Sectors Size Id Type | |||
/dev/sda1 * 2048 206847 204800 100M 83 Linux | |||
/dev/sda2 206848 48021503 47814656 22.8G 83 Linux | |||
</pre> | |||
<pre> | |||
Device Boot Start End Sectors Size Id Type | |||
/dev/sdb1 2048 2318335 2316288 1.1G 83 Linux | |||
</pre> | |||
<br /> | <br /> | ||
* '''Encrypting Partitions ( root /dev/sda2 and swap /dev/sdb1 )''' | |||
<console> | <console> | ||
# ##i## | # ##i##cryptsetup --cipher aes-xts-plain64 --hash sha512 --key-size 512 --iter-time 2500 --use-urandom luksFormat /dev/sda2 ↵ | ||
# ##i##cryptsetup --cipher aes-xts-plain64 --hash sha512 --key-size 512 --iter-time 2500 --use-urandom luksFormat /dev/sdb1 ↵ | |||
</console> | |||
<br /> | |||
* '''Initializing Encrypted Partitions''' | |||
<console> | |||
# ##i##cryptsetup luksOpen /dev/sda2 cryptroot ↵ | |||
# ##i##cryptsetup luksOpen /dev/sdb1 cryptswap ↵ | |||
</console> | </console> | ||
<br /> | |||
* '''Creating Logical Volumes''' | |||
<console> | |||
# ##i##pvcreate /dev/mapper/cryptroot ↵ | |||
# ##i##vgcreate data /dev/mapper/cryptroot ↵ | |||
# ##i##lvcreate -l 100%FREE -nroot data ↵ | |||
</console> | |||
<br /> | <br /> | ||
<console> | |||
# ##i##pvcreate /dev/mapper/cryptswap ↵ | |||
# ##i##vgcreate cswap /dev/mapper/cryptswap ↵ | |||
# ##i##lvcreate -l 100%FREE -nswap cswap ↵ | |||
</console> | |||
<br /> | <br /> | ||
* '''Creating FileSystems and Mounting them''' | |||
<console> | <console> | ||
# ##i## | # ##i##mkfs.ext2 /dev/sda1 ↵ | ||
# ##i##mkswap /dev/mapper/cswap-swap ↵ | |||
# ##i##mkfs.ext4 /dev/mapper/data-root ↵ | |||
# ##i##swapon /dev/mapper/cswap-swap ↵ | |||
# ##i##mkdir /mnt/funtoo ↵ | |||
# ##i##mount /dev/mapper/data-root /mnt/funtoo ↵ | |||
# ##i##mkdir /mnt/funtoo/boot ↵ | |||
# ##i##mount /dev/sda1 /mnt/funtoo/boot ↵ | |||
</console> | </console> | ||
<br /> | |||
* '''Install the Stage 3 tarball and chroot''' | |||
{{file|name=/etc/fstab|desc= |body= | |||
# <fs> <mountpoint> <type> <opts> <dump/pass> | |||
/dev/sda1 /boot ext2 noauto,noatime 1 2 | |||
/dev/mapper/cswap-swap none swap sw 0 0 | |||
/dev/mapper/data-root / ext4 noatime,nodiratime,defaults 0 1 | |||
}} | |||
<br /> | |||
* '''Update the System''' | |||
<console> | |||
# ##i##echo "sys-kernel/debian-sources -binary" >> /etc/portage/package.use ↵ | |||
# ##i##emerge --sync | |||
# ##i##emerge -uDavN --with-bdeps=y @world | |||
</console> | |||
<br /> | <br /> | ||
* '''Building the kernel''' | |||
{{Note| This step is very important}} | |||
<console> | <console> | ||
# ##i## cd /usr/src/linux ↵ | |||
# ##i## make menuconfig ↵ | |||
</console> | </console> | ||
{{kernelop | |||
|title= | |||
|desc= | |||
General setup ---> | |||
[*] Initial RAM filesystem and RAM disk (initramfs/initrd) support | |||
[*] Support initial ramdisks compressed using gzip | |||
}} | |||
{{kernelop | |||
|title= | |||
|desc= | |||
Device Drivers ---> | |||
Generic Driver Options ---> | |||
[*] Maintain a devtmpfs filesystem to mount at /dev | |||
}} | |||
{{kernelop | |||
|title= | |||
|desc= | |||
Device Drivers ---> | |||
SCSI device support ---> | |||
{*} SCSI device support | |||
<*> SCSI disk support | |||
<*> SCSI generic support | |||
[*] SCSI low-level drivers ---> | |||
<*> virtio-scsi support | |||
[*] Multiple devices driver support ---> | |||
<*>Device Mapper Support | |||
<*> Crypt target support | |||
Virtio drivers ---> | |||
<*> PCI driver for virtio devices | |||
[*] Support for legacy virtio draft 0.9.X and older devices | |||
<*> Virtio balloon driver | |||
<*> Virtio input driver | |||
}} | |||
{{kernelop | |||
|title= | |||
|desc= | |||
Cryptographic API ---> | |||
<*> XTS support | |||
-*-AES cipher algorithms | |||
<*> SHA256 digest algorithm (SSSE3/AVX/AVX2/SHA-NI) | |||
<*> SHA512 digest algorithm (SSSE3/AVX/AVX2) | |||
}} | |||
<br /> | |||
* '''Install GRUB2 and boot-update ebuild''' | |||
{{file|name=/etc/boot.conf|desc= |body= | |||
boot { | |||
generate grub | |||
default "Funtoo Linux" | |||
timeout 3 | |||
} | |||
"Funtoo Linux" { | |||
kernel vmlinuz[-v] | |||
initrd initramfs.cpio.gz | |||
params += enc_root=/dev/sda2 lvm luks root=/dev/mapper/data-root rootfstype=ext4 quiet | |||
} | |||
}} | |||
<br /> | |||
* '''Better-Initramfs''' | |||
<console> | |||
# ##i##cd /root && git clone https://github.com/slashbeast/better-initramfs ↵ | |||
# ##i##cd better-initramfs && make bootstrap-all && make prepare && make image && mv output/initramfs.cpio.gz /boot/ ↵ | |||
</console> | |||
* '''Install cryptsetup and lvm ebuilds''' | |||
<console> | |||
# ##i##emerge -va cryptsetup lvm2 ↵ | |||
</console> | |||
* '''Configuring Swap to be mounted during boot''' | |||
'''''The key file will be stored on encrypted file system''''' | |||
<console> | |||
# ##i##dd bs=512 count=4 if=/dev/urandom of=/etc/.swapkey iflag=fullblock ↵ | |||
# ##i##cryptsetup luksAddKey /dev/sdb1 /etc/.swapkey ↵ | |||
</console> | |||
<br /> | |||
{{file|name=/etc/conf.d/dmcrypt|desc= |body= | |||
target=cryptswap | |||
source='/dev/sdb1' | |||
key='/etc/.swapkey' | |||
}} | |||
<br /> | |||
* '''Installing bootloader to MBR and adjusting some stuff''' | |||
<console> | |||
# ##i##grub-install --target=i386-pc --no-floppy /dev/sda ↵ | |||
# ##i##boot-update ↵ | |||
# ##i##emerge rsyslog dnscrypt-proxy ↵ | |||
# ##i##rc-update add rsyslog default ↵ | |||
# ##i##rc-update add dnscrypt-proxy default ↵ | |||
# ##i##rc-update add dmcrypt boot ↵ | |||
# ##i##rc-update add lvm boot ↵ | |||
# ##i##rc-update -u ↵ | |||
</console> | |||
<br /> | |||
* '''Configuring Networking''' | |||
* ''Get IP Addresses from [https://manager.linode.com Linode Manager] '''Remote Access Tab''''' | |||
<console> | |||
# ##i##cd /etc/init.d ↵ | |||
# ##i##ln -s netif.tmpl net.eth0 ↵ | |||
# ##i##rc-update add net.eth0 default ↵ | |||
</console> | |||
{{file|name=/etc/conf.d/net.eth0|desc= |body= | |||
template="interface" | |||
ipaddrs="200.230.240.45/24 2001:948:7:7::140/64" | |||
nameservers="127.0.0.1" | |||
gateway="200.230.240.1" | |||
gateway6='fe80::1' | |||
}} | |||
<br /> | |||
<big>'''Show time!'''</big> | |||
* From [https://manager.linode.com/ Linode Manager], On '''Dashboard''' tab click '''Shutdown''' and '''Edit Configuration Profile''' | |||
* Boot Settings -> Set Kernel to '''Direct Disc''' | |||
* Filesystem/Boot Helpers -> '''Disable ALL Helpers''' | |||
<br /> | |||
Boot your Line | |||
[[Category:HOWTO]] | |||
Latest revision as of 15:15, March 4, 2017
This howto describes how to setup a complete Funtoo Encrypted Install ( Root File System and SWAP ) using LUKS and LVM on LINODE VPS
Setting Linode
- From Linode Manager create a new Linode. Under the Disks section of the Linode Dashboard, click on "Create a new Disk:"
- Label your new disk image and choose an appropriate size. Here we will create "two disks" the first for root partition and another for swap. Set appropriate size for each one.
- Select the Create a New Configuration Profile option. Assign a label, and select your disk images under Block Device Assignment.
Click on Save Changes once your profile is complete.
- Return to the Linode DashBoard, and select the Rescue tab. From there, click the Reboot Into Rescue Mode button. Your Linode will now boot into the Finnix recovery image. Use the Lish shell to access your Linode.
- Run the following set of commands to create a root password and enable SSH server:
root # passwd ↵ root # service ssh start ↵
{{{title}}}
{{{body}}}
Note
Use Funtoo Install Guide for Reference.
- MBR Partition layout
Device Boot Start End Sectors Size Id Type /dev/sda1 * 2048 206847 204800 100M 83 Linux /dev/sda2 206848 48021503 47814656 22.8G 83 Linux
Device Boot Start End Sectors Size Id Type /dev/sdb1 2048 2318335 2316288 1.1G 83 Linux
- Encrypting Partitions ( root /dev/sda2 and swap /dev/sdb1 )
root # cryptsetup --cipher aes-xts-plain64 --hash sha512 --key-size 512 --iter-time 2500 --use-urandom luksFormat /dev/sda2 ↵ root # cryptsetup --cipher aes-xts-plain64 --hash sha512 --key-size 512 --iter-time 2500 --use-urandom luksFormat /dev/sdb1 ↵
- Initializing Encrypted Partitions
root # cryptsetup luksOpen /dev/sda2 cryptroot ↵ root # cryptsetup luksOpen /dev/sdb1 cryptswap ↵
- Creating Logical Volumes
root # pvcreate /dev/mapper/cryptroot ↵ root # vgcreate data /dev/mapper/cryptroot ↵ root # lvcreate -l 100%FREE -nroot data ↵
root # pvcreate /dev/mapper/cryptswap ↵ root # vgcreate cswap /dev/mapper/cryptswap ↵ root # lvcreate -l 100%FREE -nswap cswap ↵
- Creating FileSystems and Mounting them
root # mkfs.ext2 /dev/sda1 ↵ root # mkswap /dev/mapper/cswap-swap ↵ root # mkfs.ext4 /dev/mapper/data-root ↵ root # swapon /dev/mapper/cswap-swap ↵ root # mkdir /mnt/funtoo ↵ root # mount /dev/mapper/data-root /mnt/funtoo ↵ root # mkdir /mnt/funtoo/boot ↵ root # mount /dev/sda1 /mnt/funtoo/boot ↵
- Install the Stage 3 tarball and chroot
/etc/fstab # <fs> <mountpoint> <type> <opts> <dump/pass>
/dev/sda1 /boot ext2 noauto,noatime 1 2
/dev/mapper/cswap-swap none swap sw 0 0
/dev/mapper/data-root / ext4 noatime,nodiratime,defaults 0 1
- Update the System
root # echo "sys-kernel/debian-sources -binary" >> /etc/portage/package.use ↵ root # emerge --sync root # emerge -uDavN --with-bdeps=y @world
- Building the kernel
Note
This step is very important
root # cd /usr/src/linux ↵ root # make menuconfig ↵
General setup --->
[*] Initial RAM filesystem and RAM disk (initramfs/initrd) support
[*] Support initial ramdisks compressed using gzip
Device Drivers --->
Generic Driver Options --->
[*] Maintain a devtmpfs filesystem to mount at /dev
Device Drivers --->
SCSI device support --->
{*} SCSI device support
<*> SCSI disk support
<*> SCSI generic support
[*] SCSI low-level drivers --->
<*> virtio-scsi support
[*] Multiple devices driver support --->
<*>Device Mapper Support
<*> Crypt target support
Virtio drivers --->
<*> PCI driver for virtio devices
[*] Support for legacy virtio draft 0.9.X and older devices
<*> Virtio balloon driver
<*> Virtio input driver
Cryptographic API --->
<*> XTS support
-*-AES cipher algorithms
<*> SHA256 digest algorithm (SSSE3/AVX/AVX2/SHA-NI)
<*> SHA512 digest algorithm (SSSE3/AVX/AVX2)
- Install GRUB2 and boot-update ebuild
/etc/boot.conf boot {
generate grub
default "Funtoo Linux"
timeout 3
}
"Funtoo Linux" {
kernel vmlinuz[-v]
initrd initramfs.cpio.gz
params += enc_root=/dev/sda2 lvm luks root=/dev/mapper/data-root rootfstype=ext4 quiet
}
- Better-Initramfs
root # cd /root && git clone https://github.com/slashbeast/better-initramfs ↵ root # cd better-initramfs && make bootstrap-all && make prepare && make image && mv output/initramfs.cpio.gz /boot/ ↵
- Install cryptsetup and lvm ebuilds
root # emerge -va cryptsetup lvm2 ↵
- Configuring Swap to be mounted during boot
The key file will be stored on encrypted file system
root # dd bs=512 count=4 if=/dev/urandom of=/etc/.swapkey iflag=fullblock ↵ root # cryptsetup luksAddKey /dev/sdb1 /etc/.swapkey ↵
/etc/conf.d/dmcrypt target=cryptswap
source='/dev/sdb1'
key='/etc/.swapkey'
- Installing bootloader to MBR and adjusting some stuff
root # grub-install --target=i386-pc --no-floppy /dev/sda ↵ root # boot-update ↵ root # emerge rsyslog dnscrypt-proxy ↵ root # rc-update add rsyslog default ↵ root # rc-update add dnscrypt-proxy default ↵ root # rc-update add dmcrypt boot ↵ root # rc-update add lvm boot ↵ root # rc-update -u ↵
- Configuring Networking
- Get IP Addresses from Linode Manager Remote Access Tab
root # cd /etc/init.d ↵ root # ln -s netif.tmpl net.eth0 ↵ root # rc-update add net.eth0 default ↵
/etc/conf.d/net.eth0 template="interface"
ipaddrs="200.230.240.45/24 2001:948:7:7::140/64"
nameservers="127.0.0.1"
gateway="200.230.240.1"
gateway6='fe80::1'
Show time!
- From Linode Manager, On Dashboard tab click Shutdown and Edit Configuration Profile
- Boot Settings -> Set Kernel to Direct Disc
- Filesystem/Boot Helpers -> Disable ALL Helpers
Boot your Line