The Funtoo Linux project has transitioned to "Hobby Mode" and this wiki is now read-only.
Difference between revisions of "Encrypted funtoo on linode"
Knightgats (talk | contribs) |
Knightgats (talk | contribs) |
||
| Line 88: | Line 88: | ||
Command (m for help): ##i## q ↵ | Command (m for help): ##i## q ↵ | ||
</console> | </console> | ||
<br /> | |||
'''Create Swap Partition''' | |||
<console> | <console> | ||
| Line 104: | Line 109: | ||
<console> | <console> | ||
# ##i##cryptsetup --cipher aes-xts-plain64 --hash sha512 --key-size 256 luksFormat /dev/sda2 | # ##i##cryptsetup --cipher aes-xts-plain64 --hash sha512 --key-size 256 luksFormat /dev/sda2 ↵ | ||
# ##i##cryptsetup --cipher aes-xts-plain64 --hash sha512 --key-size 256 luksFormat /dev/sdb1 | # ##i##cryptsetup --cipher aes-xts-plain64 --hash sha512 --key-size 256 luksFormat /dev/sdb1 ↵ | ||
</console> | </console> | ||
<br /> | <br /> | ||
<big>Initializing Encrypted Partitions</big> | <big>'''Initializing Encrypted Partitions'''</big> | ||
<br /> | <br /> | ||
<console> | <console> | ||
# ##i##cryptsetup luksOpen /dev/sda2 cryptroot | # ##i##cryptsetup luksOpen /dev/sda2 cryptroot ↵ | ||
# ##i##cryptsetup luksOpen /dev/sdb1 cryptswap | # ##i##cryptsetup luksOpen /dev/sdb1 cryptswap ↵ | ||
</console> | </console> | ||
<br /> | <br /> | ||
'''Creating Logical Volumes''' | <big>'''Creating Logical Volumes'''</big> | ||
<br /> | <br /> | ||
<console> | <console> | ||
# ##i##pvcreate /dev/mapper/cryptroot | # ##i##pvcreate /dev/mapper/cryptroot ↵ | ||
# ##i##vgcreate data /dev/mapper/cryptroot | # ##i##vgcreate data /dev/mapper/cryptroot ↵ | ||
# ##i##lvcreate -l 100%FREE -nroot data | # ##i##lvcreate -l 100%FREE -nroot data ↵ | ||
</console> | </console> | ||
| Line 134: | Line 139: | ||
<console> | <console> | ||
# ##i##pvcreate /dev/mapper/cryptswap | # ##i##pvcreate /dev/mapper/cryptswap ↵ | ||
# ##i##vgcreate cswap /dev/mapper/cryptswap | # ##i##vgcreate cswap /dev/mapper/cryptswap ↵ | ||
# ##i##lvcreate -l 100%FREE -nswap cswap | # ##i##lvcreate -l 100%FREE -nswap cswap ↵ | ||
</console> | </console> | ||
'''Creating FileSystems''' | <big>'''Creating FileSystems and Mounting them'''</big> | ||
<br /> | <br /> | ||
<console> | |||
# ##i##mkfs.ext2 /dev/sda1 ↵ | |||
# ##i##mkswap /dev/mapper/cswap-swap ↵ | |||
# ##i##mkfs.ext4 /dev/mapper/data-root ↵ | |||
# ##i##swapon /dev/mapper/cswap-swap ↵ | |||
# ##i##mkdir /mnt/funtoo | |||
# ##i##mount /dev/mapper/data-root /mnt/funtoo | |||
# ##i##mkdir /mnt/funtoo/boot | |||
# ##i##mount /dev/sda1 /mnt/funtoo/boot | |||
</console> | |||
Revision as of 03:01, November 17, 2016
This howto describes how to setup a complete Funtoo Encrypted Install ( Root File System and SWAP ) using LUKS and LVM on LINODE VPS
Use Funtoo Installation Guide for reference.
This howto is a compilation of steps. If you find any discrepancy blame pfctl on #Funtoo @ Freenode.
Work smarter not Harder.
Setting Linode
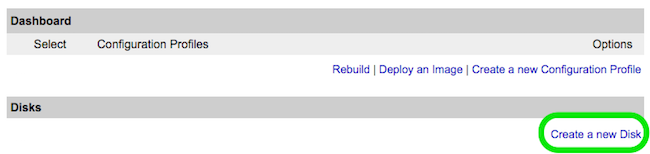
- From Linode Manager create a new Linode. Under the Disks section of the Linode Dashboard, click on "Create a new Disk:"
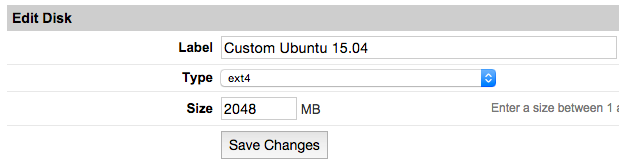
- Label your new disk image and choose an appropriate size. Here we will create "two disks" the first for root partition and another for swap. Set appropriate size for each one.
- Select the Create a New Configuration Profile option. Assign a label, and select your disk images under Block Device Assignment.
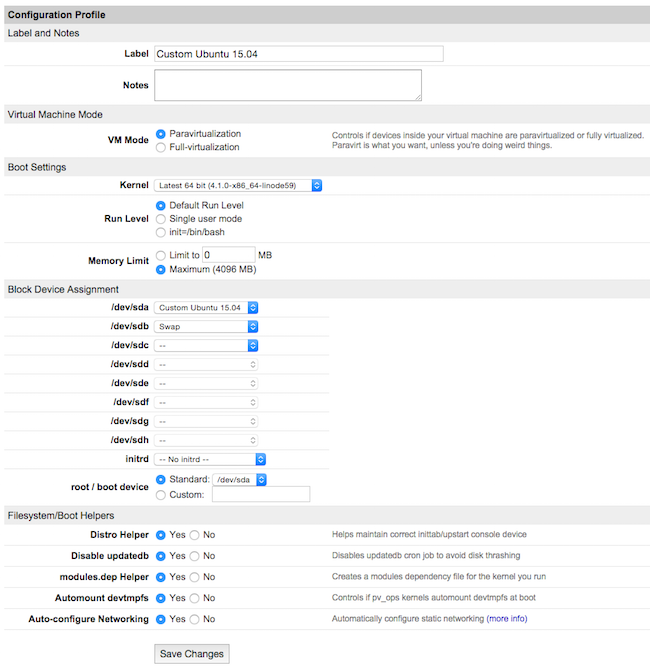
Click on Save Changes once your profile is complete.
- Return to the Linode DashBoard, and select the Rescue tab. From there, click the Reboot Into Rescue Mode button. Your Linode will now boot into the Finnix recovery image. Use the Lish shell to access your Linode.
- Run the following set of commands to create a root password and enable SSH server:
root # passwd ↵ root # service ssh start ↵
Prepare Hard Disk and Partitions
root # sgdisk --zap-all /dev/sda ↵ root # sgdisk --zap-all /dev/sdb ↵ Creating new GPT entries. GPT data structures destroyed! You may now partition the disk using fdisk or other utilities.
Now we will use fdisk to create the MBR partition table and partitions:
root # fdisk /dev/sda ↵
Within fdisk, follow these steps:
Empty the partition table:
Command (m for help): o ↵
Create Partition 1 (boot):
Command (m for help): n ↵ Partition type (default p): p ↵ Partition number (1-4, default 1): 1 ↵ First sector: ↵ Last sector: +100M ↵
Create Partition 2 (root):
Command (m for help): n ↵ Partition type (default p): p ↵ Partition number (2-4, default 2): 2 ↵ First sector: ↵ Last sector: ↵ Command (m for help): w ↵ Command (m for help): q ↵
Create Swap Partition
root # fdisk /dev/sdb ↵ Command (m for help): n ↵ Partition type (default p): p ↵ Partition number (1-4, default 1): 1 ↵ First sector: ↵ Last sector: ↵ Command (m for help): w ↵ Command (m for help): q ↵
Encrypting Partitions ( root /dev/sda2 and swap /dev/sdb1 )
root # cryptsetup --cipher aes-xts-plain64 --hash sha512 --key-size 256 luksFormat /dev/sda2 ↵ root # cryptsetup --cipher aes-xts-plain64 --hash sha512 --key-size 256 luksFormat /dev/sdb1 ↵
Initializing Encrypted Partitions
root # cryptsetup luksOpen /dev/sda2 cryptroot ↵ root # cryptsetup luksOpen /dev/sdb1 cryptswap ↵
Creating Logical Volumes
root # pvcreate /dev/mapper/cryptroot ↵ root # vgcreate data /dev/mapper/cryptroot ↵ root # lvcreate -l 100%FREE -nroot data ↵
root # pvcreate /dev/mapper/cryptswap ↵ root # vgcreate cswap /dev/mapper/cryptswap ↵ root # lvcreate -l 100%FREE -nswap cswap ↵
Creating FileSystems and Mounting them
root # mkfs.ext2 /dev/sda1 ↵ root # mkswap /dev/mapper/cswap-swap ↵ root # mkfs.ext4 /dev/mapper/data-root ↵ root # swapon /dev/mapper/cswap-swap ↵ root # mkdir /mnt/funtoo root # mount /dev/mapper/data-root /mnt/funtoo root # mkdir /mnt/funtoo/boot root # mount /dev/sda1 /mnt/funtoo/boot