The Funtoo Linux project has transitioned to "Hobby Mode" and this wiki is now read-only.
Difference between revisions of "Encrypted funtoo on linode"
Knightgats (talk | contribs) |
Knightgats (talk | contribs) |
||
| Line 325: | Line 325: | ||
key='/etc/.swapkey' | key='/etc/.swapkey' | ||
}} | }} | ||
<br /> | |||
<big>'''Installing bootloader to MBR and adjusting some stuff'''</big> | |||
<console> | |||
# ##i##grub-install --target=i386-pc --no-floppy /dev/sda | |||
# ##i##boot-update | |||
# ##i##emerge rsyslog | |||
# ##i##rc-update add dmcryt boot | |||
# ##i##rc-update add lvm boot | |||
# ##i##rc-update -u | |||
</console> | |||
Revision as of 05:04, November 17, 2016
This howto describes how to setup a complete Funtoo Encrypted Install ( Root File System and SWAP ) using LUKS and LVM on LINODE VPS
Use Funtoo Installation Guide for reference.
This howto is a compilation of steps. If you find any discrepancy blame pfctl on #Funtoo @ Freenode.
Work smarter not Harder.
Setting Linode
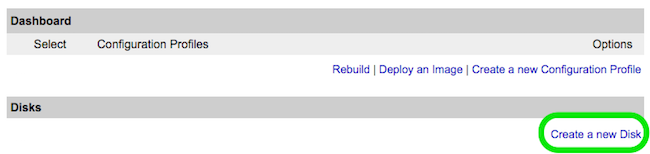
- From Linode Manager create a new Linode. Under the Disks section of the Linode Dashboard, click on "Create a new Disk:"
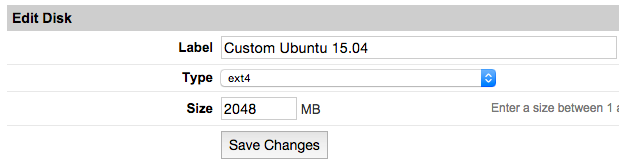
- Label your new disk image and choose an appropriate size. Here we will create "two disks" the first for root partition and another for swap. Set appropriate size for each one.
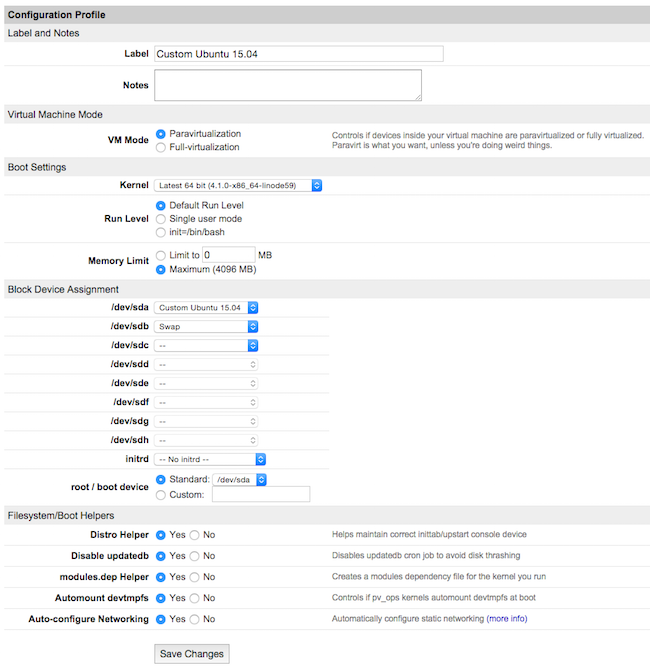
- Select the Create a New Configuration Profile option. Assign a label, and select your disk images under Block Device Assignment.
Click on Save Changes once your profile is complete.
- Return to the Linode DashBoard, and select the Rescue tab. From there, click the Reboot Into Rescue Mode button. Your Linode will now boot into the Finnix recovery image. Use the Lish shell to access your Linode.
- Run the following set of commands to create a root password and enable SSH server:
root # passwd ↵ root # service ssh start ↵
Prepare Hard Disk and Partitions
root # sgdisk --zap-all /dev/sda ↵ root # sgdisk --zap-all /dev/sdb ↵ Creating new GPT entries. GPT data structures destroyed! You may now partition the disk using fdisk or other utilities.
Now we will use fdisk to create the MBR partition table and partitions:
root # fdisk /dev/sda ↵
Within fdisk, follow these steps:
Empty the partition table:
Command (m for help): o ↵
Create Partition 1 (boot):
Command (m for help): n ↵ Partition type (default p): p ↵ Partition number (1-4, default 1): 1 ↵ First sector: ↵ Last sector: +100M ↵
Create Partition 2 (root):
Command (m for help): n ↵ Partition type (default p): p ↵ Partition number (2-4, default 2): 2 ↵ First sector: ↵ Last sector: ↵ Command (m for help): w ↵ Command (m for help): q ↵
Create Swap Partition
root # fdisk /dev/sdb ↵ Command (m for help): n ↵ Partition type (default p): p ↵ Partition number (1-4, default 1): 1 ↵ First sector: ↵ Last sector: ↵ Command (m for help): w ↵ Command (m for help): q ↵
Encrypting Partitions ( root /dev/sda2 and swap /dev/sdb1 )
root # cryptsetup --cipher aes-xts-plain64 --hash sha512 --key-size 256 luksFormat /dev/sda2 ↵ root # cryptsetup --cipher aes-xts-plain64 --hash sha512 --key-size 256 luksFormat /dev/sdb1 ↵
Initializing Encrypted Partitions
root # cryptsetup luksOpen /dev/sda2 cryptroot ↵ root # cryptsetup luksOpen /dev/sdb1 cryptswap ↵
Creating Logical Volumes
root # pvcreate /dev/mapper/cryptroot ↵ root # vgcreate data /dev/mapper/cryptroot ↵ root # lvcreate -l 100%FREE -nroot data ↵
root # pvcreate /dev/mapper/cryptswap ↵ root # vgcreate cswap /dev/mapper/cryptswap ↵ root # lvcreate -l 100%FREE -nswap cswap ↵
Creating FileSystems and Mounting them
root # mkfs.ext2 /dev/sda1 ↵ root # mkswap /dev/mapper/cswap-swap ↵ root # mkfs.ext4 /dev/mapper/data-root ↵ root # swapon /dev/mapper/cswap-swap ↵ root # mkdir /mnt/funtoo ↵ root # mount /dev/mapper/data-root /mnt/funtoo ↵ root # mkdir /mnt/funtoo/boot ↵ root # mount /dev/sda1 /mnt/funtoo/boot ↵
Installing the Stage 3 tarball and chrooting
root # cd /mnt/funtoo ↵ root # wget http://build.funtoo.org/funtoo-current/x86-64bit/generic_64/stage3-latest.tar.xz ↵ root # tar xpf stage3-latest.tar.xz ↵ root # cp /etc/resolv.conf etc/ ↵ root # mount -t proc none proc ↵ root # mount --rbind /dev dev ↵ root # mount --rbind /sys sys↵ root # chroot . bash -l ↵
Editing the fstab
root # nano /etc/fstab ↵
/etc/fstab # <fs> <mountpoint> <type> <opts> <dump/pass>
/dev/sda1 /boot ext2 noauto,noatime 1 2
/dev/mapper/cswap-swap none swap sw 0 0
/dev/mapper/data-root / ext4 noatime,nodiratime,defaults 0 1
Get the Funtoo Portage three
root # emerge --sync ↵
/etc/localtime
/etc/localtime is used to specify the timezone that your machine is in, and defaults to UTC. If you would like your Funtoo Linux system to use local time, you should replace /etc/localtime with a symbolic link to the timezone that you wish to use.
root # ln -sf /usr/share/zoneinfo/America/Sao_Paulo ↵
/etc/portage/make.conf
MAKEOPTS="-j2"
Updating Entire System.
root # echo "sys-kernel/debian-sources -binary" >> /etc/portage/package.use ↵ root # emerge -uDavN @world
Building the kernel
This step is very imporant pay attention
root # cd /usr/src/linux ↵ root # make menuconfig ↵
General setup --->
[*] Initial RAM filesystem and RAM disk (initramfs/initrd) support
[*] Support initial ramdisks compressed using gzip
[*] Support initial ramdisks compressed using bzip2
[*] Support initial ramdisks compressed using LZMA
[*] Support initial ramdisks compressed using XZ
[*] Support initial ramdisks compressed using LZO
[*] Support initial ramdisks compressed using LZ4
Device Drivers --->
Generic Driver Options --->
[*] Maintain a devtmpfs filesystem to mount at /dev
Device Drivers --->
SCSI device support --->
{*} SCSI device support
<*> SCSI disk support
<*> SCSI generic support
[*] SCSI low-level drivers --->
<*> virtio-scsi support
[*] Multiple devices driver support --->
<*>Device Mapper Support
<*> Crypt target support
Virtio drivers --->
<*> PCI driver for virtio devices
[*] Support for legacy virtio draft 0.9.X and older devices
<*> Virtio balloon driver
<*> Virtio input driver
Cryptographic API --->
<*> XTS support
-*-AES cipher algorithms
<*> SHA256 digest algorithm (SSSE3/AVX/AVX2/SHA-NI)
<*> SHA512 digest algorithm (SSSE3/AVX/AVX2)
Compile and install
root # make && make modules_install ↵ root # rm /boot/* ↵ root # make install ↵
Installing GRUB2 and boot-update ebuild
root # emerge grub boot-update
Editing the boot.conf
root # nano /etc/boot.conf ↵
/etc/boot.conf boot {
generate grub
default "Funtoo Linux"
timeout 3
}
"Funtoo Linux" {
kernel vmlinuz[-v]
initrd initramfs.cpio.gz
}
"Funtoo Linux genkernel" {
kernel kernel[-v]
initrd initramfs[-v]
params += enc_root=/dev/sda2 lvm luks root=/dev/mapper/data-root rootfstype=ext4 quiet
}
Better-Initramfs
root # cd /opt/ ↵ root # git clone https://github.com/slashbeast/better-initramfs ↵ root # cd better-initramfs ↵ root # make -j2 bootstrap-all ↵ root # make prepare ↵ root # make image ↵ root # cp output/initramfs.cpio.gz /boot/
Check if cryptsetup and lvm ebuilds are installed if not emerge them
root # emerge -s crypsetup lvm2
Configuring Swap to be mounted during boot The key file will be stored on encrypted file system
root # dd bs=512 count=4 if=/dev/urandom of=/etc/.swapkey iflag=fullblock root # cryptsetup luksAddKey /dev/sdb1 /etc/.swapkey
Editing the dmcrypt
root # nano /etc/conf.d/dmcrypt ↵
/etc/conf.d/dmcrypt target=cryptswap
source='/dev/sdb1'
key='/etc/.swapkey'
Installing bootloader to MBR and adjusting some stuff
root # grub-install --target=i386-pc --no-floppy /dev/sda root # boot-update root # emerge rsyslog root # rc-update add dmcryt boot root # rc-update add lvm boot root # rc-update -u