The Funtoo Linux project has transitioned to "Hobby Mode" and this wiki is now read-only.
Difference between revisions of "UEFI Secure Boot and SHIM"
(Created page with "= Introduction = This page describes how to set up secure boot on Funtoo Linux with GRUB 2 + SHIM, using genkernel and ego boot update. The resulting secure boot chain is:...") |
|||
| (One intermediate revision by one other user not shown) | |||
| Line 30: | Line 30: | ||
= Installing tools and Secure Boot Certificates = | = Installing tools and Secure Boot Certificates = | ||
Install {{c|efitools}}, {{c|mokutil}}, {{c|shim}}, {{c|grub2} and {{c|sbsigntools}}: | Install {{c|efitools}}, {{c|mokutil}}, {{c|shim}}, {{c|grub2}} and {{c|sbsigntools}}: | ||
{{console|body= | {{console|body= | ||
| Line 128: | Line 128: | ||
== Rebooting pc == | == Rebooting pc == | ||
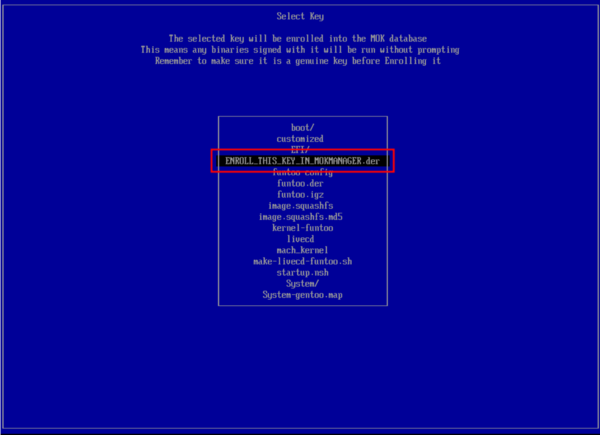
Now, reboot your pc and check if secure boot is enabled. Perhaps it will come into MokManager at bootloader automatically. There are three options: "Reboot", "Enroll key from disk" and "Enroll hash from disk". Chose "Enroll key from disk", select certificate '''ENROLL_THIS_KEY_IN_MOKMANAGER.der''' and confirm. Reboot. | Now, reboot your pc and check if secure boot is enabled. Perhaps it will come into MokManager at bootloader automatically. There are three options: "Reboot", "Enroll key from disk" and "Enroll hash from disk". Chose "Enroll key from disk", select certificate '''ENROLL_THIS_KEY_IN_MOKMANAGER.der''' and confirm. Reboot. | ||
[[File:Mokmanager-enroll-key.png|600px]] | |||
== After reboot == | == After reboot == | ||
Latest revision as of 03:05, January 9, 2023
Introduction
This page describes how to set up secure boot on Funtoo Linux with GRUB 2 + SHIM, using genkernel and ego boot update. The resulting secure boot chain is:
- The firmware has UEFI secure boot certificates installed, and you hold the corresponding private keys.
- GRUB is signed by your key registered in the UEFI secure boot signature database.
- GRUB can be locked down when booted on a secure boot environment. On a locked down configuration, the GRUB will be restricted and some operations/commands cannot be executed.
- The Secure Boot Advanced Targeting (SBAT) is a mechanism to allow the revocation of components in the boot path by using generation numbers embedded into the EFI binaries. The SBAT metadata is located in an .sbat data section that has set of UTF-8 strings as comma-separated values (CSV). See https://github.com/rhboot/shim/blob/main/SBAT.md for more details.
- The "shim" loader is a small bootloader for UEFI based x86_64 machines. It is signed by the Microsoft UEFI CA, which is embedded in all UEFI BIOSes. The shim contains the Fedora Secure Boot CA key which is the base of the Funtoo secure boot trust chain.
- SHIM may be useful if your machine's firmware doesn't allow you to install your own secure boot certificates.
- SHIM only checks signatures of the boot loader and kernel, but not the GRUB config file or initramfs, which opens your machine to attacks.
- GRUB have SHIM official support, has been released in 2.06 version.
Prerequisites
This guide assumes that:
- You have a bootable Funtoo LiveCD in case something goes wrong.
- Your machine's firmware allows you to install your own secure boot certificates.
- You have a working Funtoo installation with full disk encryption over LVM.
- You have signed kernel module support.
- You are using the GRUB 2 bootloader installed on the EFI boot partition.
- Enter the firmware setup utility and put secure boot in setup mode.
- The boot partition is VFAT mounted on
/boot.
Having full disk encryption is critical; without it, the attacker can take out your hard disk and change anything but kernel, initramfs and bootloader.
Installing tools and Secure Boot Certificates
Install efitools, mokutil, shim, grub2 and sbsigntools:
root # emerge -av sys-boot/shim sys-boot/grub app-crypt/efitools app-crypt/sbsigntools sys-boot/mokutil
Decide where you want to keep your keys. You may keep them on the hard disk (not recommended), on another machine or on an external drive.
Follow these steps to generate new certificate valid for 10 years reading this doc: Signed_kernel_module_support
This is NOT optional, it is a requirement for Secure Boot to have signed modules.
Mount your boot partition and create new EFI dir:
root # mount /boot root # mkdir -p /boot/EFI/BOOT
Create a new /boot/sbat.csv file:
/boot/sbat.csv sbat,1,SBAT Version,sbat,1,https://github.com/rhboot/shim/blob/main/SBAT.md
grub,1,Free Software Foundation,grub,2.06,https://www.gnu.org/software/grub/
Create a new grub image with all necessary modules and files:
root # grub-mkimage --directory "/usr/lib/grub/x86_64-efi" --prefix "/grub" --output "/boot/EFI/BOOT/grubx64_real.efi" --format 'x86_64-efi' --compression 'auto' file blocklist test true regexp newc search at_keyboard usb_keyboard gcry_md5 hashsum gzio xzio lzopio ext2 xfs read halt sleep serial terminfo png password_pbkdf2 gcry_sha512 pbkdf2 part_gpt part_msdos ls tar squash4 loopback part_apple minicmd diskfilter linux relocator jpeg iso9660 udf hfsplus halt acpi mmap gfxmenu video_colors trig bitmap_scale gfxterm bitmap font fat exfat ntfs fshelp efifwsetup reboot echo configfile normal terminal gettext chain priority_queue bufio datetime cat extcmd crypto gzio boot all_video efi_gop efi_uga video_bochs video_cirrus video video_fb gfxterm_background gfxterm_menu zfs tpm --sbat /boot/sbat.csv root # cp -rp /usr/lib/grub/x86_64-efi/ /boot/EFI/BOOT/
Sign required files on startup
Sign the kernel using the keys and certificate created following these steps Signed_kernel_module_support:
Copy certificate to /boot partition:
root # cp /etc/kernel/certs/linux/signing_key.der /boot/ENROLL_THIS_KEY_IN_MOKMANAGER.der
root # sbsign --key /etc/kernel/certs/linux/signing_key.asc --cert /etc/kernel/certs/linux/signing_key.cert --output /boot/kernel-debian-sources-x86_64-6.1.4_p1-signed /boot/kernel-debian-sources-x86_64-6.1.4_p1 root # mv /boot/kernel-debian-sources-x86_64-6.1.4_p1 /boot/kernel-debian-sources-x86_64-6.1.4_p1.old root # mv /boot/kernel-debian-sources-x86_64-6.1.4_p1-signed /boot/kernel-debian-sources-x86_64-6.1.4_p1
Sign shim files:
root # sbsign --key /etc/kernel/certs/linux/signing_key.asc --cert /etc/kernel/certs/linux/signing_key.cert --output /boot/EFI/BOOT/mmx64.efi /usr/share/shim/mmx64.efi root # sbsign --key /etc/kernel/certs/linux/signing_key.asc --cert /etc/kernel/certs/linux/signing_key.cert --output /boot/EFI/BOOT/bootx64.efi /usr/share/shim/BOOTX64.EFI
Sign grub image:
root # sbsign --key /etc/kernel/certs/linux/signing_key.asc --cert /etc/kernel/certs/linux/signing_key.cert --output /boot/EFI/BOOT/grubx64.efi /boot/EFI/BOOT/grubx64_real.efi
Enroll MOK certificate with mokutil
Maybe you need delete all keys in the system first, including the Platform Key.
After you delete all keys, the system is forced to immediately disable Secure Boot. Secure Boot remains disabled upon system reboot until valid secure boot keys are restored.
From the System Utilities screen, select System Configuration > BIOS/Platform Configuration (RBSU) > Server Security > Secure Boot Settings > Advanced Secure Boot Options > Delete all keys. Press Enter to delete all keys and confirm the deletion.
Import the DER format key generated and converted from above steps:
root # mokutil --import /etc/kernel/certs/linux/signing_key.der --ignore-keyring
Check and confirm the new imported key which to be enrolled:
root # mokutil --list-new
The Boot Manager
In order to select the correct extension that will load the operating system, EFI provides to the user an internal boot manager. The operating system is responsible for creating a new entry for itself. We can launch the boot manager, and list all the boot entries, during the power on process, usually pressing F9 or F12. But we can use the efibootmgr tool to query and edit the entries. For example, to list the current entries we can run efibootmgr -v. Ex:
root # efibootmgr -v BootCurrent: 0000 Timeout: 0 seconds BootOrder: 2001,0001,0002 Boot0001* UEFI Onboard LAN IPv4 PciRoot(0x0)/Pci(0x1c,0x0)/Pci(0x0,0x0)/MAC(74867af80e6e,0)/IPv4(0.0.0.00.0.0.0,0,0)RC Boot0002* UEFI Onboard LAN IPv6 PciRoot(0x0)/Pci(0x1c,0x0)/Pci(0x0,0x0)/MAC(74867af80e6e,0)/IPv6([::]:<->[::]:,0,0)RC Boot2001* EFI USB Device RC
You need to remove unnecessary entries first, ex:
root # efibootmgr --delete-bootnum --bootnum 2001 root # efibootmgr --delete-bootnum --bootnum 0001 root # efibootmgr --delete-bootnum --bootnum 0002
Now, create the required entry:
root # efibootmgr --unicode --create --label "Funtoo Linux" --disk /dev/sdb --part 1 --loader /boot/EFI/BOOT/bootx64.efi
Rebooting pc
Now, reboot your pc and check if secure boot is enabled. Perhaps it will come into MokManager at bootloader automatically. There are three options: "Reboot", "Enroll key from disk" and "Enroll hash from disk". Chose "Enroll key from disk", select certificate ENROLL_THIS_KEY_IN_MOKMANAGER.der and confirm. Reboot.
After reboot
Check if your system load with secure boot enabled. Ex:
root # dmesg | grep -i secureboot [ 0.000000] secureboot: Secure boot enabled
root # dmesg | grep integrity | grep -i X.509 [ 2.175720] integrity: Loading X.509 certificate: UEFI:db [ 2.175753] integrity: Loaded X.509 cert 'Microsoft Corporation UEFI CA 2011: 13adbf4309bd82709c8cd54f316ed522988a1bd4' [ 2.175755] integrity: Loading X.509 certificate: UEFI:db [ 2.175776] integrity: Loaded X.509 cert 'Microsoft Windows Production PCA 2011: a92902398e16c49778cd90f99e4f9ae17c55af53' [ 2.176034] integrity: Loading X.509 certificate: UEFI:MokListRT (MOKvar table) [ 2.176252] integrity: Loaded X.509 cert 'Fedora Secure Boot CA: fde32599c2d61db1bf5807335d7b20e4cd963b42' [ 2.176253] integrity: Loading X.509 certificate: UEFI:MokListRT (MOKvar table) [ 2.176457] integrity: Loaded X.509 cert 'Funtoo Secure Boot: b94a4c04d23948ca4c5d52409ae93242a80df9a8'
Confirm the enrolled certificate:
root # mokutil --list-enrolled
List the keys in db:
root # mokutil --db
You can enable the validation process in shim. You might get the "Booting in insecure mode" warning while loading shim. This will enable secure boot validation for the OS. Do keep in mind this will prevent unsigned kernel modules from loading. You can remove it with the following command:
root # mokutil --enable-validation
If you want to disable it, run:
root # mokutil --disable-validation
If you need debug:
root # mokutil --set-verbosity true root # mokutil --set-fallback-verbosity true